Guides
Provisioning Pro Data
Understanding how containers can transform your workflow.
Pro Data combines all twelve SSDs into a pool of storage that is allocated among one or more distinct logical containers for data organization, protection, and privacy. This guide outlines how containers can promote collaboration, describing unique properties that can improve your workflow.
Pro Data is incredibly versatile: it can be used as one large volume or divided among projects, tasks, collaborators, or any combination that makes sense for your current or future workflow. Up to 15 containers can be provisioned dynamically and without interruption of service, making on-the-fly reconfiguration seamless.
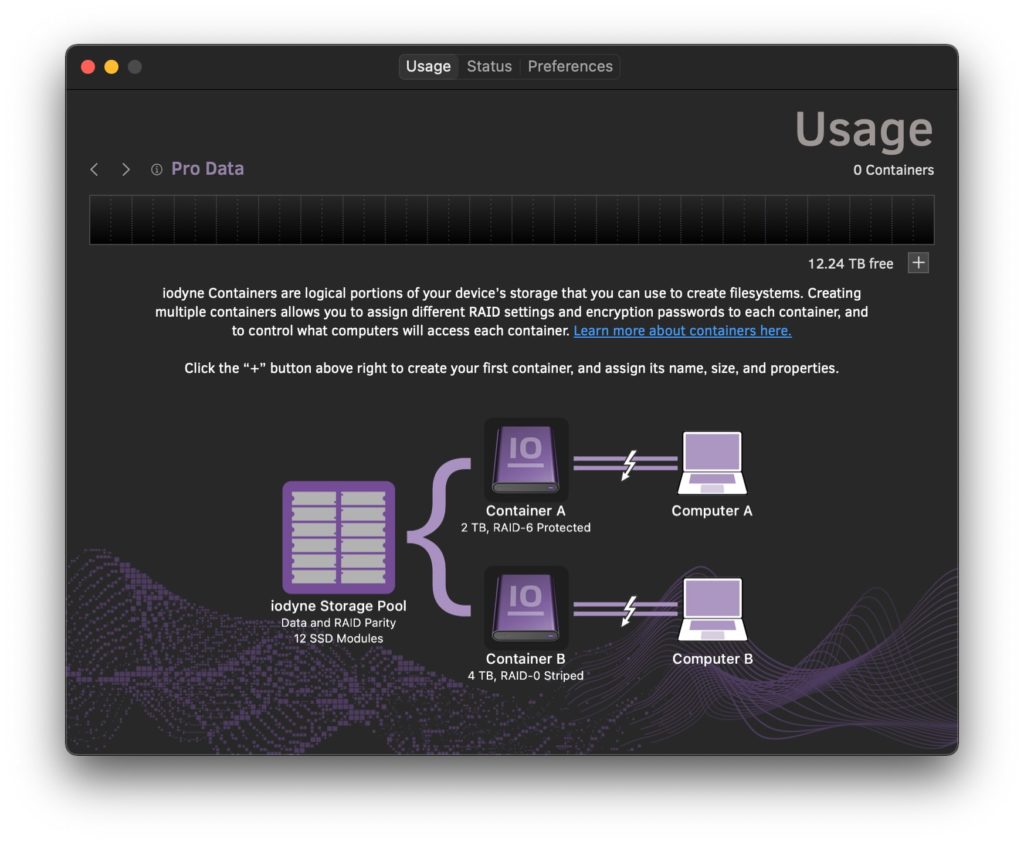
Containers can perhaps most easily be understood as virtual storage devices, as though connecting a computer to a handful of drives with a single cable. Pro Data containers do not correlate to specific SSDs or specific SSD regions, however: instead, all SSDs are aggregated for performance and redundancy, and containers are dynamically provisioned across the entire storage pool.
Pro Data containers also allow you to share and handoff storage when connecting multiple computers to a single device, by dividing large projects into parallel tasks. Each connected computer in the workflow can attach one or more containers for the files it will need. Containers can then be handed off between computers instantly without recabling. For example, a film editor may handoff a container of raw footage for color correction while receiving assets from a VFX artist for review. Media management software that watches folders for new assets can run on an unattended computer to automatically create proxies to be shared over a network or uploaded to the Cloud.
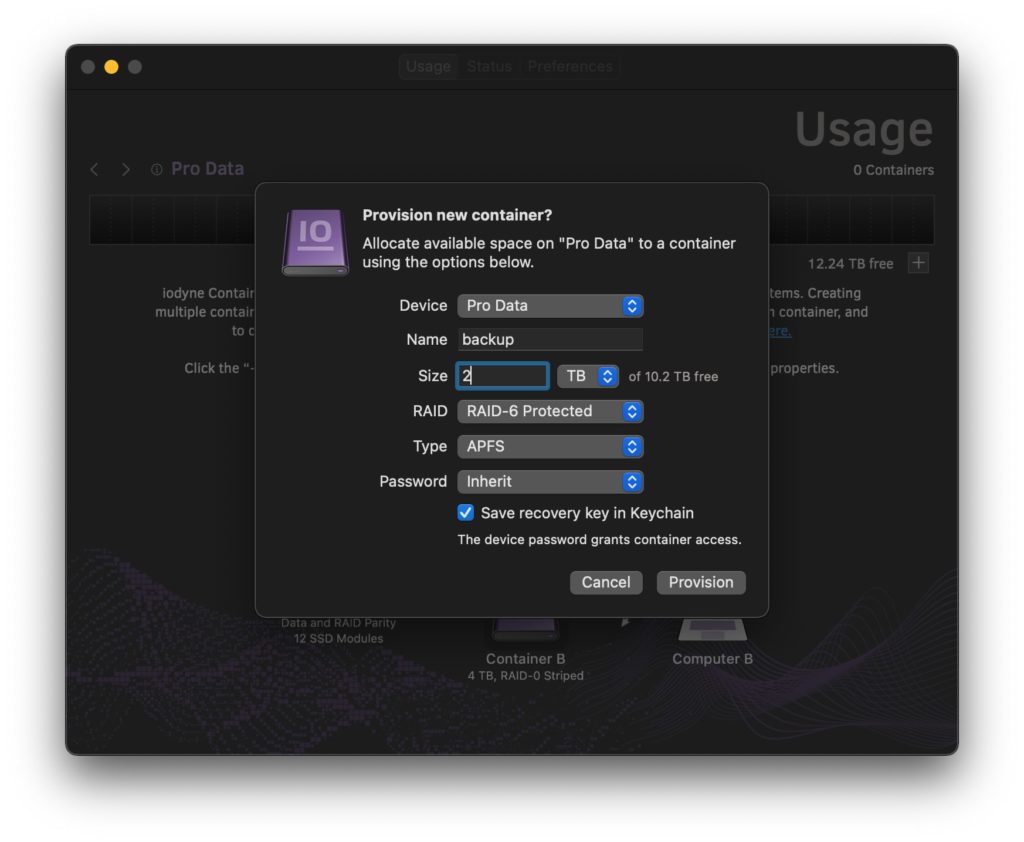
Each container has a descriptive name and a size allocation, expressed as either a quantity of gigabytes (GB) or terabytes (TB) or percentage of the free space in the storage pool. The following sections detail other properties that inform your options when creating new containers.
RAID Levels
For decades, multiple drives have been used in parallel: distributing workload to improve performance and storing the summation of correlating bits called parity by which data can be safely reconstituted should a device go offline or fail. This method is referred to as RAID.1
By default, Pro Data containers are created with a redundancy profile of RAID-6 to provide the most robust protection against data loss in the event of up to two device failures. The amount of overhead incurred by RAID-6 parity in Pro Data is roughly 1/6th of the storage allocated, represented as an aggregate from all RAID-6 containers in the Usage tab capacity graph.
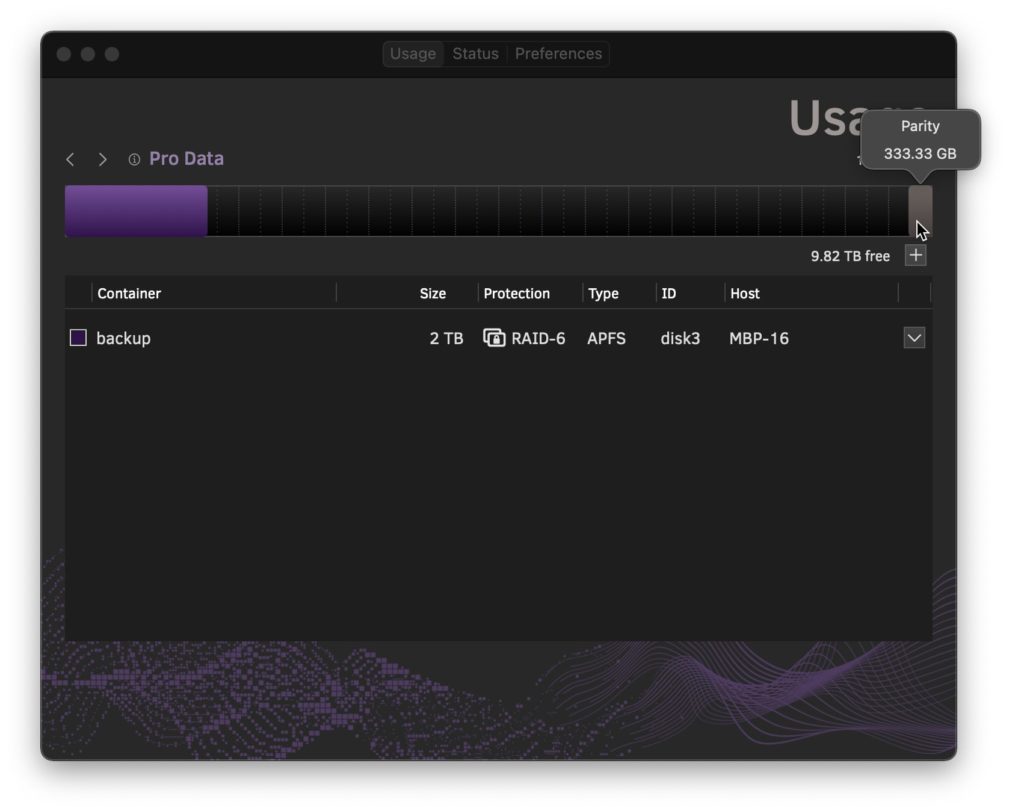
In certain cases where data is temporary, backed up remotely, or easily regenerated from source materials, such as render files or scratch space, RAID-0 prioritizes storage efficiency and may improve performance.
Filesystem Types
Nearly all containers are assigned a designated filesystem, such as APFS or exFAT, in order to present a filesystem volume for Open and Save to your applications. For the rare use cases that do not require a filesystem, an unformatted Raw option is provided. You can also format Raw containers using Disk Utility.
Conventional external SSDs often ship formatted as exFAT for cross-platform compatibility. However, macOS computers can take advantage of the modern attributes of APFS such as snapshots for faster, more efficient backups, and instant file cloning.2 APFS supports one or more volumes per container, and APFS volumes can be shared over the network to other Mac, Windows or Linux computers using NFS or SMB file sharing.
Passwords
Securing against unauthorized access is fundamental to the design of Pro Data: all data is hardware-encrypted with XTS-AES-256, and encryption keys are stored in a Secure Enclave.3 Containers can be further protected with a unique, custom password or inherit the common device password for convenience.
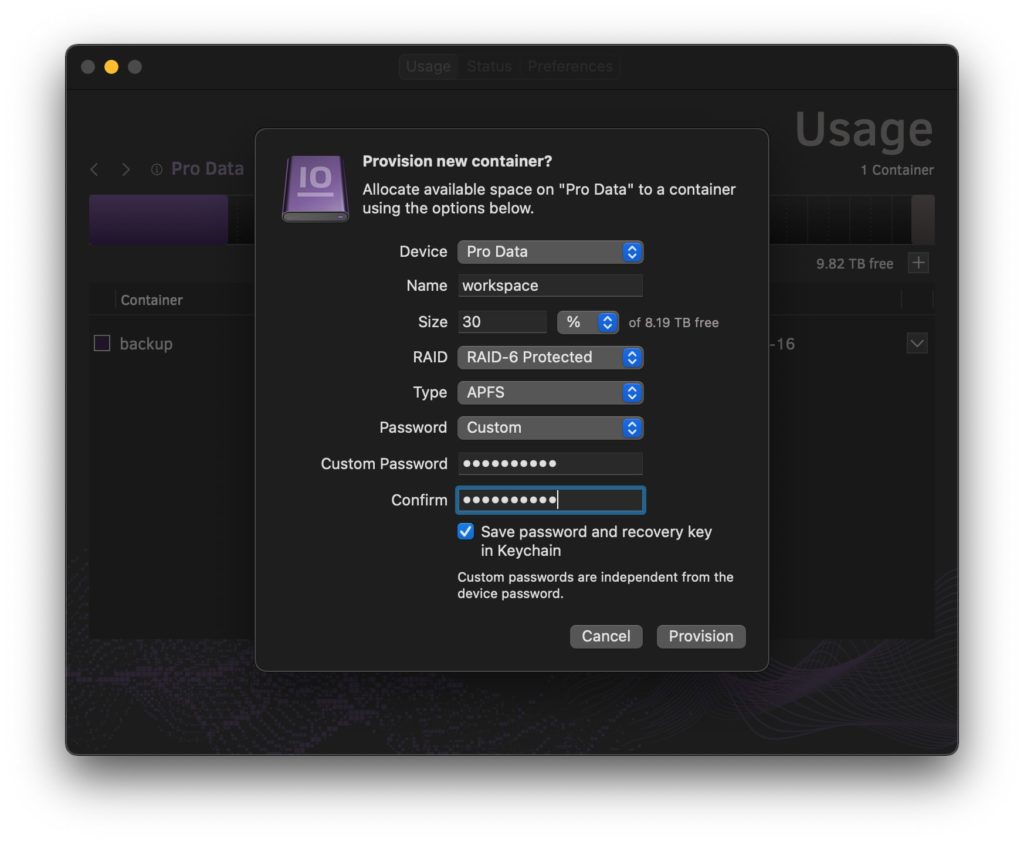
Custom passwords and recovery keys are stored in the macOS Keychain by default. In the event of a lost custom password not stored in the Keychain, the device password can be used to gain access to a container.
Conclusion
We hope this brief overview has provided some insights into how Pro Data containers can add flexibility to your workflow. Please let us know if we can help plan your deployment by emailing us at [email protected]
Footnotes:
- See Wikipedia for more information about standard RAID levels. ↩︎
- To learn more about APFS, see Apple’s Developer documentation. ↩︎
- Some operating systems and applications offer their own filesystem encryption; you can safely turn these features off when using Pro Data containers to dedicate more compute resources to your workload. ↩︎


